Malware stands for 'malevolent software,' which refers to any program that engages in malicious behavior. Malware and malicious code are phrases that are used interchangeably.
Malware comes in a variety of shapes and sizes, as well as several categories, such as viruses, Trojans, worms, spyware, botnet malware, ransomware, and so on.
Many cyberattacks on the Internet are carried out through malware, including nation-state cyberwar, criminality, fraud, and scams.
Trojans, for example, may create a backdoor into a government network, allowing nation-state attackers to steal confidential data. Ransomware may encrypt data on a user's computer, rendering it inaccessible to the user, and only allowing the data to be decrypted when the user pays a fee.
Many Distributed Denial-of-Service (DDoS) assaults, as well as spam and phishing, are carried out via botnet malware.
To better comprehend cyberattacks and build effective remedies, we need to investigate the mechanisms underlying malware generation and dissemination.
The complexity and durability of both cyber defense measures and malware technologies and operating models have grown as the political and financial stakes have risen.
For example, to evade malware detection systems, attackers now use obfuscation techniques like packing and polymorphism, as well as metamorphism , and they set up adaptive network infrastructures on the Internet to support malware updates, command-and-control, and other logistics like data transits.
In summary, malware research is growing more vital, but also more difficult.
We'll go through a malware taxonomy, as well as their usual destructive actions, eco-systems, and support infrastructure.
After that, we'll go over the tools and strategies for analyzing malware behavior, as well as network and host-based detection methods for detecting malware activity, as well as forensic analysis and attribution processes and techniques for responding to malware assaults.
A MALWARE TAXONOMY.
Malware comes in a variety of forms . The creation of a taxonomy to systematically categorize the huge range of malware kinds is instructive.
This taxonomy defines the common properties of each form of malware and may therefore be used to drive the creation of countermeasures for an entire malware category (rather than a specific malware).
Our taxonomy may encompass several dimensions due to the different features of malware technology and attack activities that can be used to categorize and label malware.
We'll go through a handful of the more crucial ones here. It's worth noting that other, more specialized features, such as target CPU architecture or operating system, might also be employed.
The first axis of our taxonomy is whether malware is a stand-alone (or independent) program or only a set of instructions to be implanted in another program.
Once installed and launched on a compromised system, standalone malware is a full application that can function on its own.
Worms and botnet malware, for example, are examples of this sort of malware.
The second kind requires the execution of a host program, i.e., it must infect a program on a computer by injecting its instructions into the program, causing the malware instructions to be executed as well.
Document macro infections and malicious browser plug-ins, for example, are examples of this sort.
In general, standalone malware is simpler to detect since it is a separate application or running process that may be spotted by the operating system or security solutions.
The second factor to consider is whether malware is persistent or not.
The majority of malware is installed in persistent storage (usually a file system) as independent malware or as an infection of another software that already has a persistent storage presence.
Other malware is memory-resident, which means that once the computer is restarted or the infected running software terminates, it is gone from the system.
Many anti-virus programs that depend on file scanning are unable to identify memory-resident malware.
Such ephemeral malware also has the benefit of being simple to clean up (or cover-up) when it has completed its assault.
The traditional method for malware to become memory-resident is to delete the malicious program (which had previously been downloaded and installed) from the file system as soon as it has been run.
Newer methods use system administration and security technologies like PowerShell to directly inject malware into memory .
According to one report , meterpreter malware was downloaded and injected into memory using PowerShell instructions following an initial vulnerability that resulted in the unauthorized execution of PowerShell, and it gathered passwords on the compromised machine.
The third dimension, which only relates to persistent malware, classifies malware according to whatever tier of the system stack it is installed and runs on.
Firmware, boot-sector, operating system kernel, drivers and Application Programming Interfaces (APIs), and user applications are the layers in increasing sequence.
Lower-layer malware is often more difficult to detect and remove, and it causes more damage since it has more power over the affected machine.
On the other hand, since there are more limits, such as a more constrained programming environment in terms of both the kinds and quantity of code permitted, it is also more difficult to build malware that can be implanted at a lower layer.
The fourth dimension is whether malware is initiated by a user activity or runs and spreads automatically.
When auto-spreading malware starts, it searches the Internet for additional susceptible devices, compromises them, and installs itself on them; the malware copies on these newly infected machines then do the same – run and propagate.
Auto-spreading malware may obviously propagate swiftly via the Internet, exponentially increasing the number of vulnerable systems.
User-activated malware, on the other hand, is installed on a computer when a user unintentionally downloads and runs it, such as by clicking on an attachment or URL in an email.
More crucially, while this virus can 'spread' by sending email with itself as an attachment to contacts in the user's address book, this spreading is not effective until the recipient of the email activates the malware.
The fifth dimension is whether malware is static, or only updated once, or constantly updated.
Most current malware is backed by infrastructure that allows a hacked computer to get a software update from a malware server, which results in the installation of a new version of the malware on the infected machine.
There are several advantages to upgrading malware from the attacker's perspective.
Updated malware, for example, may elude detection systems based on the features of previous malware samples.
The sixth factor is whether malware operates alone or as part of a larger network (i.e., a botnet).
While botnets are responsible for many assaults such as DDoS, spam, phishing, and other kinds of targeted attacks, standalone malware has grown more widespread.
That is, malware may be tailored to infect a target company and carry out destructive operations based on the company's assets that are valuable to the attacker.
To prevent detection, most current malware employs some type of obfuscation (and hence we do not explicitly include obfuscation in this taxonomy).
A virus creator may employ a variety of obfuscation methods and tools that are publicly accessible on the Internet.
Polymorphism, for example, may be exploited to evade detection approaches that rely on malware code 'signatures' or patterns.
That is, the malware's recognizable traits are altered to make each instance unique.
As a result, malware instances vary in appearance, yet they all perform the identical malicious functions.
Packing, which involves compressing and encrypting a portion of the infection, and rewriting recognizable bad instructions into other comparable instructions are two popular polymorphic malware tactics.
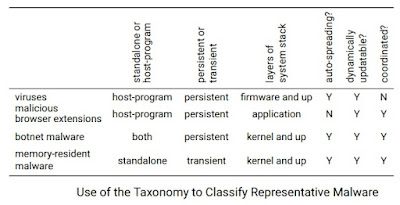
As an example, we may apply this taxonomy to a variety of malware kinds (or names). Take a look at the table below:
A virus, in particular, requires the execution of a host-program since it infects it by injecting a harmful code sequence into the program.
When the host software starts, the malicious code is executed, and it might hunt for other applications to infect in addition to completing the specified destructive operations.
A virus is usually persistent, residing in all layers of the system stack except the hardware.
It can propagate on its own because it can autonomously insert itself into applications.
If a virus can connect to a malware update server, it may also be dynamically updated.
Although the technique for mutation is built in the virus's own code, a polymorphic malware virus may change itself so that fresh copies seem different.
A virus isn't usually part of a coordinated network since, although it may infect a large number of computers, the viral code doesn't usually undertake coordinated actions.
Malicious browser plug-ins and extensions, scripts (e.g., JavaScript on a web page), and document macros are examples of malware that need a host application (e.g., macro viruses and PDF malware).
These sorts of malware may be disguised and constantly updated.
They can also create a coordinated network.
Any malware that is part of a coordinated network with a botnet architecture that offers command-and-control is referred to as botnet malware.
Malware updates and other logistical assistance are frequently provided via botnet infrastructure.
Botnet malware is persistent and frequently obfuscated, living in the kernel, driver, or application layers.
Some botnet malware, such as malicious browser plug-ins and extensions, need a host application and user activation to propagate (e.g., malicious JavaScript).
Other botnet malware is stand-alone and spreads automatically across the Internet by infecting weak machines or users.
Trojans, keyloggers, ransomware, click bots, spam bots, mobile malware, and other malware are examples.
PUPs (Potentially Unwanted Programs)
A potentially undesirable program (PUP) is usually a piece of code that is downloaded as part of a valuable software.
When a user downloads the free edition of a mobile gaming app, for example, adware, a kind of PUP that shows ad banners on the game window, may be installed.
Adware often gathers user data (such as geo-location, time spent playing the game, friends, and so on) without the user's knowledge or agreement in order to provide more targeted adverts to the user and increase the advertising's efficacy.
Adware is classified as spyware in this scenario, which is described as an undesirable application that steals data about a computer and its users.
PUPs exist in a gray area because, although most download agreements offer information about these dubious behaviors, most users do not study the finer details and so do not comprehend what they are installing.
PUPs should be classified as malware from the standpoint of cybersecurity, and this is the approach used by many protection solutions.
The basic explanation is that a PUP has the ability to evolve into full-fledged malware; once installed, the user is completely dependent on the PUP operator.
For example, spyware included in a spellchecker browser extension might collect information about the user's preferred websites.
It may, however, collect user account information such as logins and passwords.
In this situation, the spyware has evolved from a PUP to a malware.
Find Jai on Twitter | LinkedIn | Instagram
You may also want to read and learn more Technology and Engineering here.
You may also want to read and learn more Cyber Security Systems here.